Ametlik GrapheneOS müük annetab

Teie koduruuter on lihtsaim tagauks, mille kaudu saab luurata kõike, mida te internetis teete
Ei ole oluline, kas kasutate VPN-i või turvalist brauserit Kui teie ruuter on häkitud, võivad nad teid luurata.
Think turning off your phone protects you? Your device carries two unique codes that follow you everywhere. These codes, known as IMEI (International Mobile Equipment Identity) and IMSI (International Mobile Subscriber Identity), are crucial for the operation of mobile networks. Every phone, regardless of its brand or model, is assigned these two identifiers during manufacturing. They serve as your phone’s fingerprint and your SIM card’s serial number, linking you to your mobile service provider.
You can’t change them. This permanence can lead to serious privacy concerns. These codes are embedded in the hardware, making them immutable and unremovable. And they’re constantly broadcasting your presence to network providers.
You can’t hide them.
Every time your phone connects to a mobile network, it leaves a trace. Every call, text, or data request effectively contributes to your location history. No apps needed. Your phone continuously shares its unique identity with every network it encounters. This means there’s no digital footprint to erase. There’s no escaping the trace it leaves behind. No browsing. The reality is that your device is perpetually active in terms of network communication. Even if you delete your apps or clear your browsing history, your phone still transmits data. Even when inactive, it’s always connected in some capacity. Just sitting in your pocket.
➔ What phone you use
➔ Which tower you connect to
➔ Where you are
➔ Which line is yours
➔ When you swap SIMs
➔ Even who was nearby
This thread explains what IMEI and IMSI are, why they’re dangerous for your privacy, how they track you, and how to reduce that risk. Recognizing these identifiers can empower you to make informed decisions regarding your mobile usage and privacy. By understanding the implications of these identifiers, you can take steps to better protect your personal information. Stay aware and take measures to minimize the exposure of your personal information.
The International Mobile Equipment Identity (IMEI) is a unique number hardcoded into your device, like a license plate. This number is essential for ensuring that each mobile device can be uniquely identified, thereby enhancing security and tracking. You can’t change it easily.
Used to:
➔ Identify your phone
➔ Block stolen devices
➔ Link your movements to the same device, even with a new SIM
The International Mobile Subscriber Identity (IMSI) stored on your SIM card, it ties your line to your network.
It reveals:
➔ What SIM you’re using
➔ Who your provider is
➔ If you changed SIMs
➔ If it’s still the same person (based on phone or behavior)
IMEI + IMSI = complete surveillance.
This combination of identifiers helps cellular companies monitor usage patterns, which can be essential for both marketing and service improvements.
Every time your smartphone connects to a cellular tower, it sends out your IMEI (International Mobile Equipment Identity) and IMSI (International Mobile Subscriber Identity) in unencrypted cleartext. This means that the information can be intercepted and read by third parties who may be monitoring network traffic.
Cell towers keep detailed logs which include:
➔ Time of connection
➔ Geographical location of the device
➔ Your individual device’s ID along with your SIM card ID
➔ Often, the IDs and locations of other nearby phones as well
This compilation of data builds a comprehensive and detailed map of your movements, interactions, and associations over time, allowing for tracking of not just where you go, but patterns in your behaviors and routines.
➔ Your mobile service carrier, who can utilize this data for various purposes
➔ Intelligence agencies and governmental bodies interested in monitoring communications
➔ Operators of cell towers, who have direct access to the information collected
➔ Forensics teams that analyze this information for investigative purposes
➔ Occasionally, individuals with malicious intent, such as criminals utilizing rogue devices (like Stingrays) to facilitate unauthorized tracking
This type of tracking does not need user permission or warnings. It runs quietly in the background, unnoticed by most people. It constantly collects information about your location and activities.
You can’t eliminate it entirely, but you can lower exposure:
✓ Use phones that randomize IMEI (rare)
✓ Change both SIM and phone regularly
✓ Use GrapheneOS or de-Googled phones
✓ Use airplane mode often
✓ Prefer WiFi + VPN + Tor (when pssible)
✓ In extreme cases: use anonymous burner phones
✓ Don’t register your SIM with real ID if possible
➔ Don’t fall for the “I’ve got nothing to hide” trap
Example
➔ You change your number and SIM. Still use the same phone? Tracked via IMEI.
➔ You change phones. Keep the SIM? Tracked via IMSI.
➔ You change both, but keep the same habits, location, and timing? Your pattern gives you away
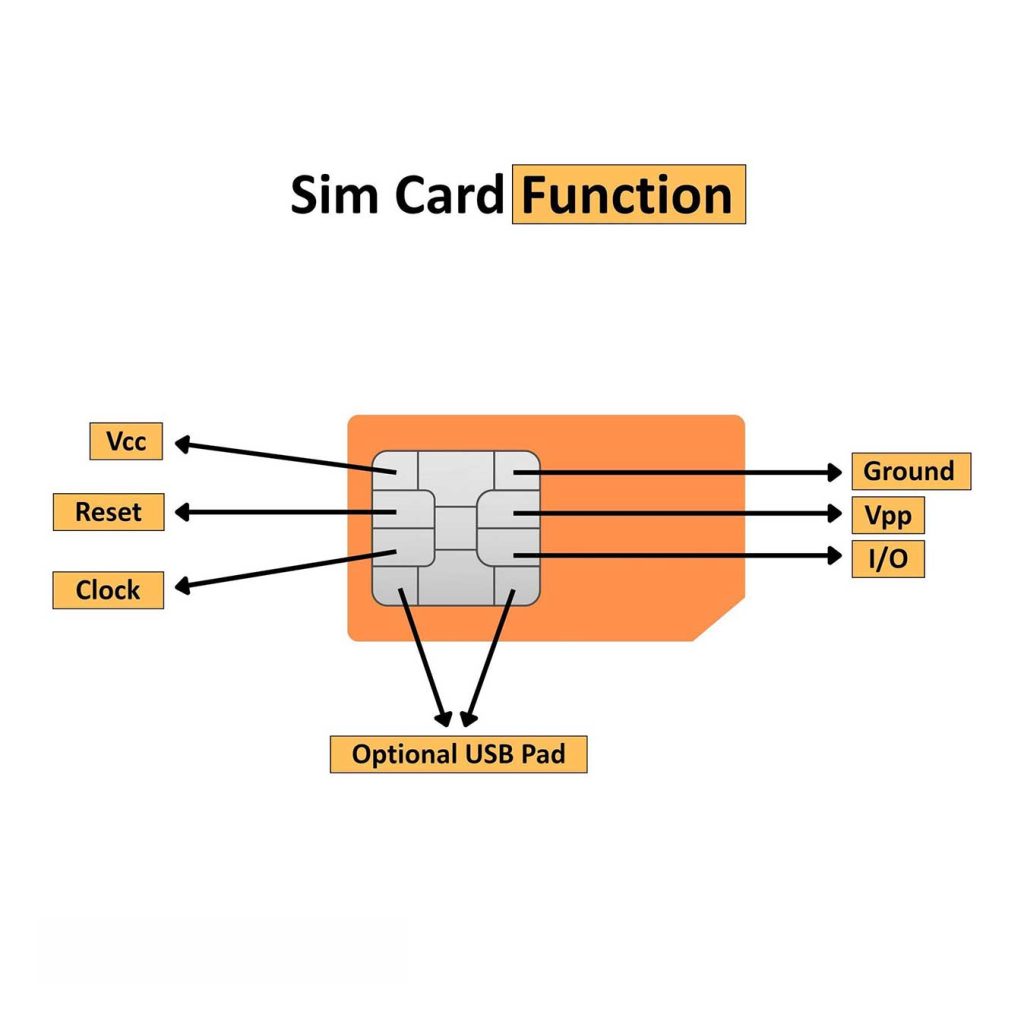
Understanding SIM Card functions
✓ Vcc – Provides power to the SIM card (1.8V / 3V / 5V)
✓ Reset – Restarts or initializes the SIM card
✓ Clock – Sends timing signals for communication
✓ Ground (GND) – Common reference point
✓ Vpp – Used in older SIMs for programming; not common now
✓ I/O – Manages data exchange between the phone and SIM
✓ Optional USB Pads – Found in some advanced SIM cards for USB connections
These pins enable secure communication, network access, and storage of mobile identity.
Now that you know how they track you on the network level, what can you do with your phone to reduce your footprint? I will explain step by step what you need so your phone it stops being a spy in your pocket like usual.
First, it is highly recommended that you stop using SIM cards directly in your device. Instead, consider utilizing a router for a much better experience. For example, our Secure Portable Router 4G E750V2, which features VPN encryption, is an excellent choice for maintaining both security and connectivity. By using this router, you can enhance your online safety while enjoying seamless internet access on multiple devices.
Your browser tracks you more than you might think. Most web browsers collect data about your online activities using cookies and other tools. This information can show advertisers and others your habits and browsing history. To protect your privacy from this tracking, we’ve set up a premium VPN on your device that encrypts your internet connection and prevents unwanted monitoring. We’ve also disabled some screen recording features in the browser to further enhance your privacy, so no screenshots can be taken of your browser window. This helps keep your online activities confidential. Additionally, you can use the TOR browser on your device for extra anonymity and security while browsing the internet.
But your phone… it gives you away.
It knows where you are, who you’re talking to, when you sleep, what you want, and what you fear.
This means that it could potentially reveal your activities and personal habits to third parties. Even turned off, it keeps gathering info But you’re not tied to this system. By making simple adjustments to your settings, you can enhance your privacy significantly.
You can take back control.
The ideal: Cryptvice secure Cryptphone + Crypthub secure portable router
It’s the most private combo you can get nowadays and what we did to reduce your tracking?
It’s not about installing 20 apps at once. It’s a step-by-step process from buying a device to delivering it with your privacy in mind. Every change matters: one app, fewer permissions, a chat with a friend.
Where did you start? What app is essential on your private phone? You can reach out to us through various channels to help install it and make the necessary adjustments. After purchasing our device, we can guide you on app installations and settings focused on privacy.
✓ Device purchased privately
✓ DeGoogled the device with a secure Android-based operating system
✓ Operating System installation and app setup is done over a secure, encrypted connection checked weekly for leaks
✓ Uses trusted apps like Threema, Silent Circle, and premium VPNs such as iVPN, Mullvad, and ProtonVPN, bought securely
✓ Virtual numbers available for messengers upon request
✓ No devices or app accounts are stored in our database
✓ Removing unnecessary app permissions
✓ Only authorized apps that prioritize privacy are used
✓ Shipping worldwide is available, with pickup at a nearby location
✓ Payments can be made via bank transfer or cryptocurrency for privacy. Ensure your wallet is private, or find a local crypto trader for assistance.
Loe lähemalt Cryptvice'i ettevõtte ja meeskonna kohta siin.
Loe lähemalt meie kohandatud seadmete kohta siin.

Ei ole oluline, kas kasutate VPN-i või turvalist brauserit Kui teie ruuter on häkitud, võivad nad teid luurata.
Oleme kasutanud ja soovitanud GrapheneOSi alates 2020. aastast Me juhime IT-firmat, mis pakub klientidele kogu maailmas võrguteenuseid.
Ühendame