Le vendite ufficiali di GrapheneOS donano
Stiamo donando 10 euro per ogni installazione di GrapheneOS che facciamo
We’ve been using and recommending GrapheneOS since 2020 We run an IT company that provides online services to clients worldwide
Le vendite ufficiali di GrapheneOS donano
Le vendite ufficiali di GrapheneOS donano
Many people are unknowingly sharing their data. In this post, I’ll show you how to check if you’re one of them and how to fix it quickly.
Your browser needs to find the right website every time you type an address. That’s the role of DNS servers.
The issue?
➔ By default, you use your internet provider’s DNS
➔ These DNS servers keep records of your searches, habits, and activities
Even if you use a VPN or clear your history, the information is still stored. It can be sold or used against you.
What’s the problem?
➔ Your DNS requests go outside the secure tunnel
➔ Your ISP can monitor the websites you visit
➔ Your “anonymity” is lost quickly
✓ Many believe VPN = safety
But if your DNS isn’t secure, you are at risk.
But you’re using 1.1.1.1, 8.8.8.8, or your ISP’s DNS. That means even if your traffic is encrypted, the sites you visit might still leak outside the tunnel. This isn’t just a small mistake, it’s one of the most common privacy failures.
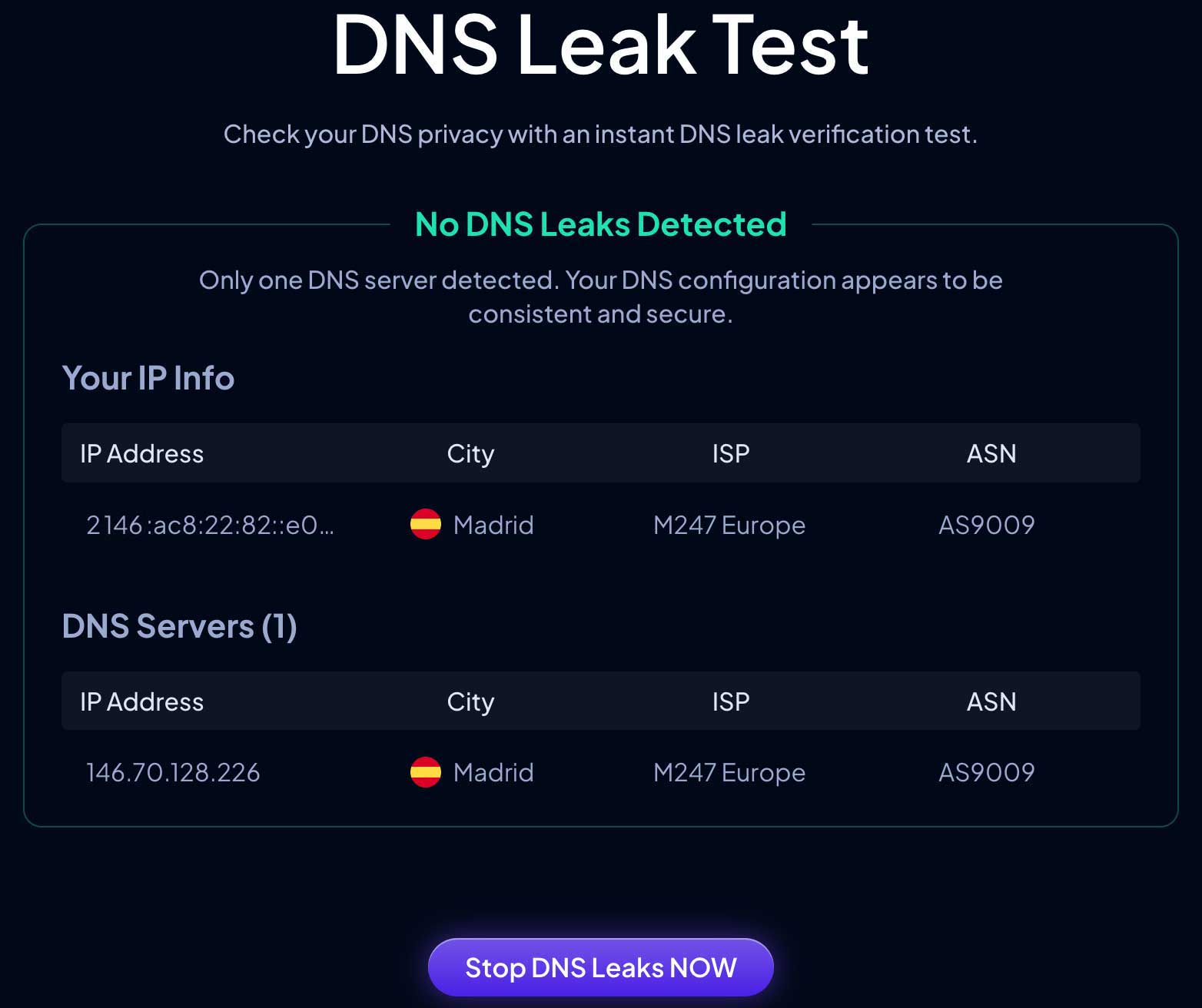
But if your VPN doesn’t have its own DNS, or if your setup is wrong, your DNS queries might leak. What does this mean? You believe you’re safe, but your requests could be handled by Google or your provider. Many think a VPN hides everything, but DNS leaks can occur. Ensure your VPN has its own secure DNS to avoid revealing more than you think. You can use tools like:
www.controld.com/tools/dns-leak-test
They can help check if your DNS requests are leaking outside your VPN.
Popular VPNs like Mullvad and iVPN offer built-in protection against DNS, IPv6, and WebRTC leaks, but this only works if they are updated and set up correctly.
⚠️ Caution: Some apps use fixed DNS servers, which can ignore your VPN settings and expose your data. This is known as “DNS hardcoding.”
To stay protected, use privacy-focused public DNS like Quad9 (blocks malware) or AdGuard DNS (blocks ads, trackers, and harmful sites; supports secure DNS methods: DoH, DoT, DNSCrypt).
On Android, apps like RethinkDNS and NetGuard allow you to control how apps resolve domain names, keeping you safe even if an app tries to bypass your VPN.
Organisations like the 14 Eyes countries use this information for broad surveillance. That’s why using tools like Tor or multi-hop VPNs is important to make it harder to track you. Want to really protect your privacy? Just encrypting isn’t enough; you also need to hide your metadata.
Read also: Organizzazioni come 14 Eyes raccolgono e condividono i vostri metadati per la sorveglianza di massa.
Now that you understand the importance of protecting your data, here are some simple tools and habits I use to reduce risks:
Privacy is an ongoing journey, not a final goal.
✓ Device purchased privately
✓ DeGoogled the device with a secure Android-based operating system
✓ Operating System installation and app setup is done over a secure, encrypted connection checked weekly for leaks
✓ Uses trusted apps like Threema, Silent Circle, and premium VPNs such as iVPN, Mullvad, and ProtonVPN, bought securely
✓ Virtual numbers available for messengers upon request
✓ No devices or app accounts are stored in our database
✓ Removing unnecessary app permissions
✓ Only authorized apps that prioritize privacy are used
✓ Shipping worldwide is available, with pickup at a nearby location
✓ Payments can be made via bank transfer or cryptocurrency for privacy. Ensure your wallet is private, or find a local crypto trader for assistance.
Read more about Cryptvice business and team here.
Read more about our customize devices here.
We’ve been using and recommending GrapheneOS since 2020 We run an IT company that provides online services to clients worldwide

From chat control to total control The EU is not just interested in your messages anymore; it wants to access
Connettiamoci