Palantir is tracking everything you do — and how to protect yourself
Best secure phone 2025
Google Pixel 9 GrapheneOS VPN Encrypted
Google Pixel 9a GrapheneOS VPN Encrypted
Best secure router 2025
CryptHub V2 Portable 4G VPN Encrypted Router
CryptHub V3 Portable 4G VPN Encrypted Router
There’s a company that helps the CIA track targets, assists ICE in deporting people, predicts crimes before they happen, and monitors employees at the world’s largest banks. It’s worth over $300 billion. And most people have never heard of it.
The company is Palantir Technologies. Founded with CIA seed money in 2003 by Peter Thiel, it builds software that pulls together massive amounts of data — phone records, financial transactions, social media, surveillance feeds, licence plates, medical records — and finds patterns humans would never spot.
Governments use it to find terrorists. Militaries use it to fight wars. Police use it to predict who might commit a crime. And corporations use it to monitor their own employees. In 2025, Palantir secured nearly $1 billion in federal contracts and signed a $10 billion deal with the U.S. Army — the largest military software contract of its kind.
This guide explains what Palantir actually does, who it works for, what data it processes, and — most importantly — what you can do to reduce the amount of data that ends up in systems like this.
How did Palantir start?
It started with fear. After September 11, 2001, the U.S. intelligence community realised it had the data to prevent the attacks — but it was scattered across dozens of agencies that didn’t talk to each other. The CIA, FBI, NSA — all sitting on pieces of the puzzle, none able to see the full picture.
Peter Thiel, the PayPal co-founder and Silicon Valley billionaire, saw an opportunity. His idea: build software that could connect all of it. Every database, every agency, every data point — linked together in one interface.
Venture capitalists thought it was too risky. Too weird. Then In-Q-Tel — the CIA’s venture capital arm — invested $2 million. Palantir’s first client was America’s spy agency.
The company is named after the “seeing stones” in Tolkien’s Lord of the Rings — the Palantíri, crystal balls that let their wielders see across vast distances. In the story, the stones were powerful tools, but they also corrupted everyone who used them. The name may be more fitting than Palantir intended.
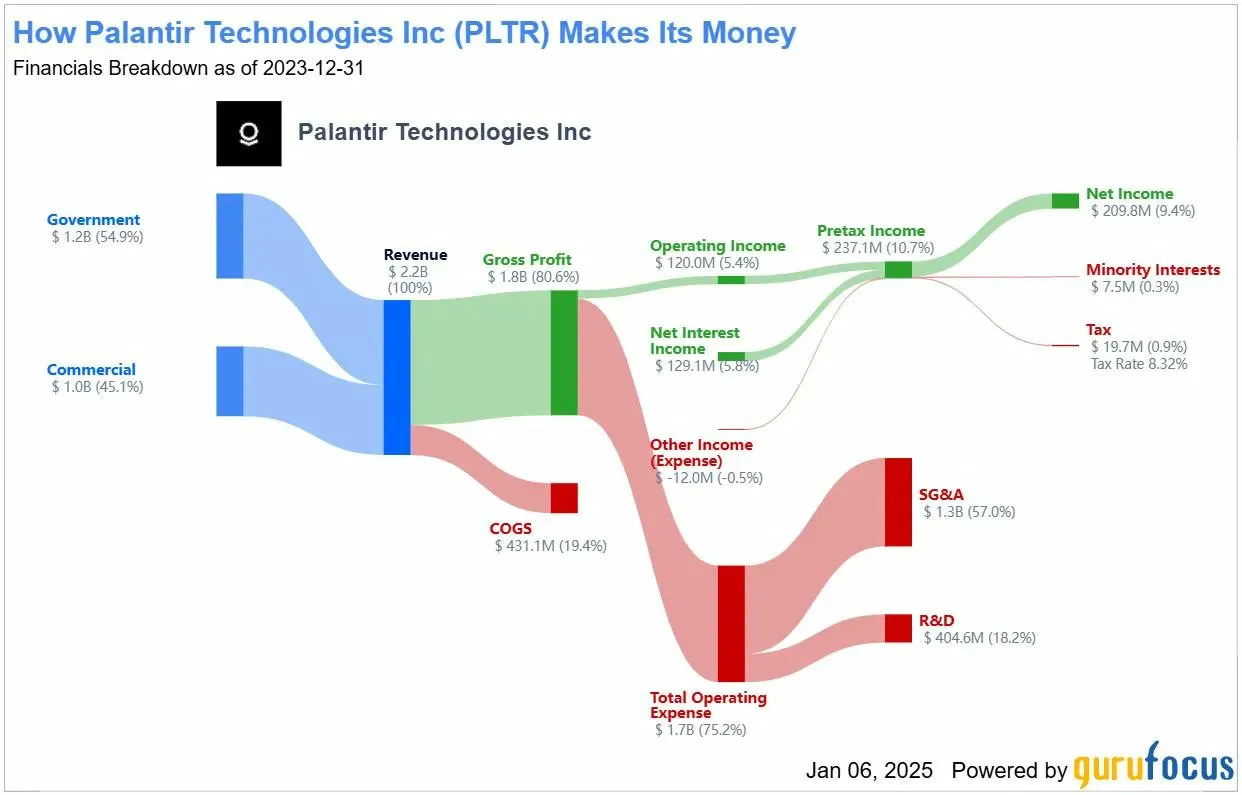
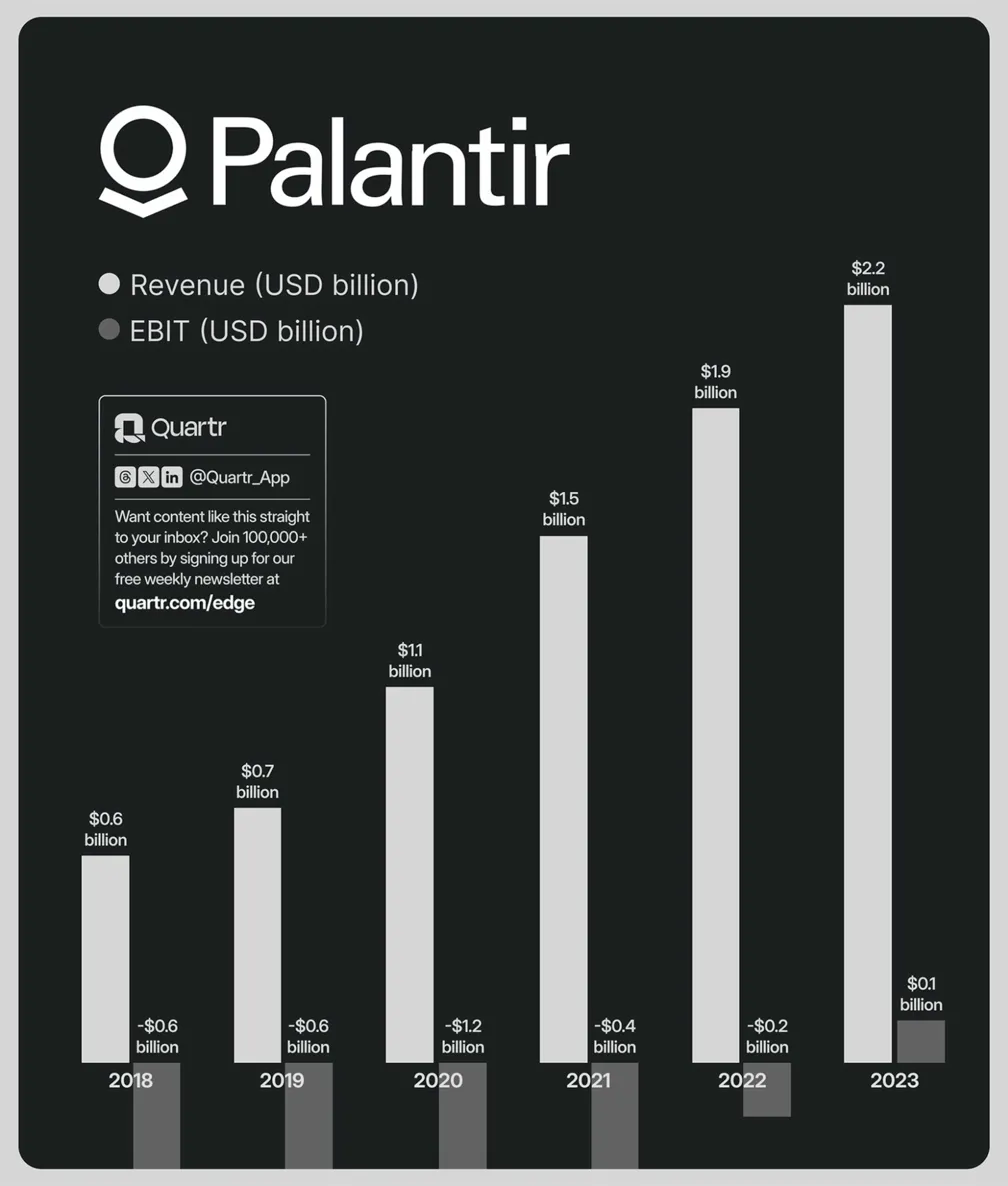
From that CIA seed money, the company grew quietly for years. It operated in secrecy, serving intelligence agencies and military units. It took 17 years to turn a profit. But by 2025, it was valued at over $300 billion — as much as Bank of America — and its software was embedded across hospitals, militaries, police departments, and federal agencies worldwide.
What does Palantir actually do?
Palantir doesn’t collect data itself. It does something potentially more powerful: it connects data that already exists and makes it searchable, analysable, and actionable.
Think of it this way: the IRS has your tax records. Social Security has your benefits data. ICE has immigration records. Your phone company has your call logs. Your bank has your transactions. Each database is relatively harmless on its own. But connect them all together, cross-reference everything, and suddenly you have a complete picture of a person’s life — where they go, who they talk to, what they buy, what they earn, who they know.
That’s exactly what Palantir’s software does. And it does it across two main products:
Gotham — for governments and intelligence agencies
Think of it as a search engine for spies. Gotham pulls together phone logs, surveillance feeds, financial records, licence plate data, social media, and classified intelligence into a single interface. Analysts can map networks, track targets in real time, and uncover hidden relationships between people, places, and events. This is the software that was used in the operation that tracked down Osama bin Laden. It’s used by the CIA, NSA, FBI, the UK’s GCHQ, and military forces across NATO.
Foundry — for corporations and civilian agencies
Foundry takes the same approach but applies it to business and government operations. It unifies messy internal data — finance, logistics, HR, supply chain, health records — into a single platform. Airbus uses it to predict aircraft component failures. Ferrari’s F1 team uses it to optimise race strategy. Hospitals use it to forecast ICU demand. And as of 2025, at least four major U.S. federal agencies use Foundry for data management, including the Department of Homeland Security and the Department of Health and Human Services.

Where is Palantir being used right now?
The scale of Palantir’s deployment in 2025 is staggering. Here are the documented cases:
U.S. Military — $10 billion contract
In August 2025, the U.S. Army signed a $10 billion, 10-year deal with Palantir — consolidating 75 separate data and software contracts into one. Palantir’s Maven Smart System, originally a $480 million Pentagon contract for AI-powered surveillance and object detection, was boosted to $1.3 billion. The system can autonomously detect, tag, and track objects or humans from drone footage, satellite imagery, and surveillance aircraft. Google originally held this contract but dropped it after employee protests. Palantir picked it up.
Immigration enforcement — ImmigrationOS
ICE awarded Palantir $30 million to build “ImmigrationOS” — a platform that identifies people for deportation, tracks self-departures in near real-time, and streamlines the removal process. It pulls data from passport records, Social Security files, IRS tax data, licence plate readers, and more. A related tool called ELITE (Enhanced Leads Identification & Targeting for Enforcement) generates dossiers on individuals and assigns confidence scores to their current addresses.
UK National Health Service — £330 million
In 2023, NHS England awarded Palantir a seven-year, £330 million contract to build a Federated Data Platform connecting patient data across England’s healthcare system. Medical professionals protested outside NHS headquarters in 2024, demanding cancellation over privacy concerns and Palantir’s military contracts.
UK Ministry of Defence — £315 million
The UK MoD awarded Palantir £75 million in 2022 and another £240 million in December 2025 for data analytics across all security classifications, including NATO interoperability.
Dutch Police — secret deployment since 2011
In 2025, the Dutch Justice Minister confirmed that Dutch police had been using Palantir software since 2011 — a fact that had remained largely undisclosed for over a decade. When researchers requested transparency, 99% of released documents were redacted.
Total federal contracts in 2025: nearly $1 billion
Palantir’s U.S. federal contracts grew from $4.4 million in 2009 to $541 million in 2024 to $970.5 million in 2025. The company has received over $900 million in federal contracts since the current administration took office.
What has gone wrong?
Not all of Palantir’s use cases involve catching terrorists or optimising supply chains. The documented abuses paint a troubling picture:
New Orleans — secret predictive policing (2012–2018)
In 2012, Palantir partnered with the New Orleans Police Department to run a predictive policing programme. The software analysed arrest records, criminal histories, social media activity, and gang affiliations to generate a list of roughly 3,900 people flagged as potential perpetrators or victims of violence. The programme was disguised as “philanthropy” and never went through public procurement. City council members didn’t know it existed. Defence attorneys were never told the software was used against their clients. When The Verge exposed it in 2018, the city didn’t renew the contract.
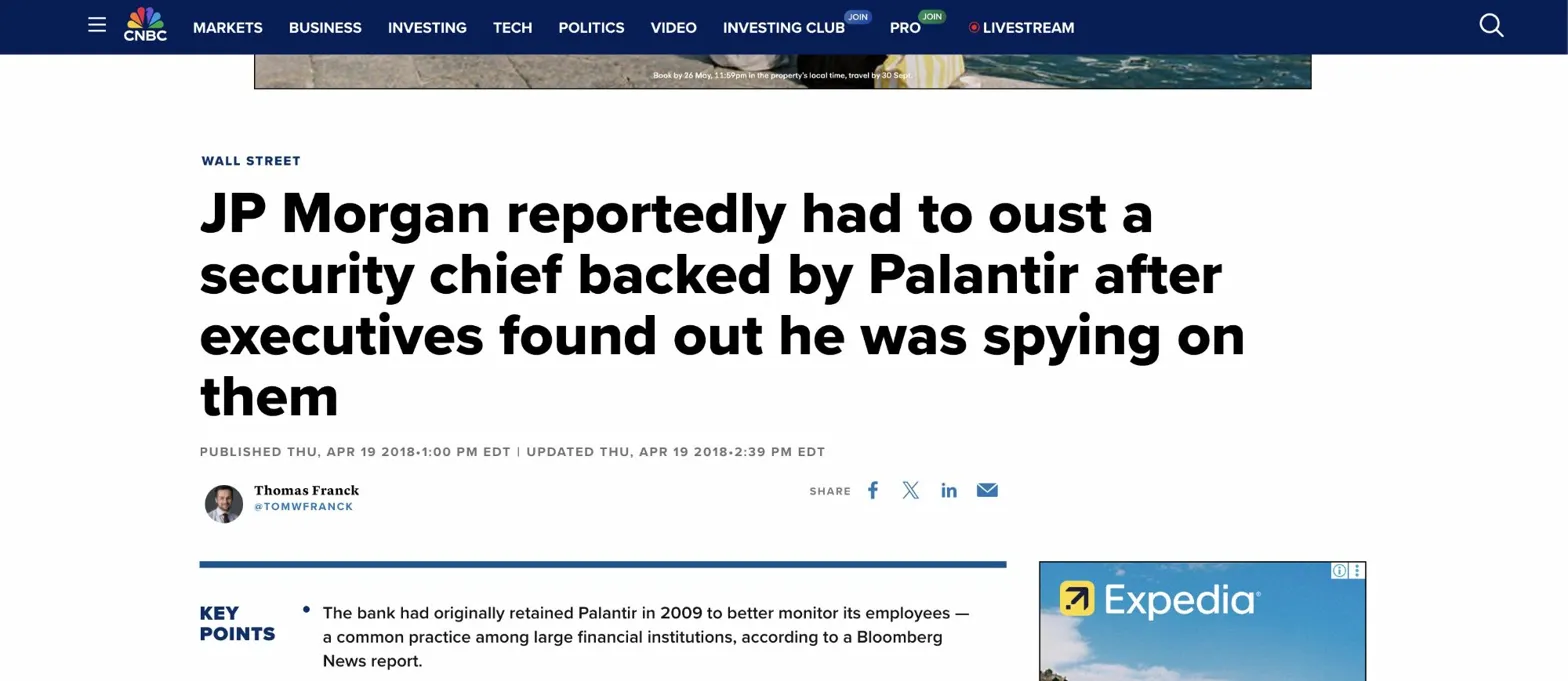
JP Morgan — employee surveillance (2009–2018)
JP Morgan hired Palantir in 2009 to monitor its own employees. The software tracked emails, web browsing, badge swipes, and phone calls. According to Bloomberg reporting in 2018, a security chief backed by Palantir was ousted after executives discovered he was using the system to spy on them. Nothing inside the building was private.
Los Angeles — biased policing
LAPD used Palantir’s software to create lists of “chronic offenders.” Investigations found the system disproportionately targeted minority neighbourhoods, essentially automating racial bias in existing police data. The programme was eventually scrapped after public outcry.
ICE — immigration targeting
Palantir has been ICE’s primary technology partner for years. Its software has been used to track air travel, analyse driver’s licence scans, and locate people using cell phone records. The ELITE tool generates individual dossiers on potential deportation targets. Some Palantir engineers have publicly raised concerns about the ethical implications of building systems designed for mass surveillance and enforcement.
The pattern: Palantir builds powerful tools, deploys them quietly, and the abuses only surface years later through investigative journalism or legal challenges. By then, the data has already been collected and the damage done.
Why should you care?
You might think: “I’m not a terrorist. I’m not an immigrant. I don’t work at JP Morgan. Why does this matter to me?”
Here’s why:
Your data is already in these systems.
Palantir’s software connects government databases. If you have a driver’s licence, a tax record, a social security number, a phone plan, or a bank account — your data exists in systems that Palantir can integrate. In March 2025, an executive order was signed requiring every federal agency to share their data. Tax records, health data, immigration files, surveillance logs — all flowing into platforms like Foundry.
The cross-referencing is the danger.
Your IRS data alone is relatively harmless. Your phone records alone are relatively harmless. Your medical records alone are relatively harmless. But when an AI system connects your tax filings to your location data, your phone contacts, your browsing habits, your medical visits, and your social media — it builds a complete profile of who you are, what you believe, who you know, and what you might do next.
There’s no opt-out.
You didn’t consent to your data being fed into Palantir’s systems. There’s no checkbox. No notification. No way to request deletion. The data was collected by government agencies and corporations you interact with every day, and Palantir’s software just connects it all.
The infrastructure is permanent.
Once these systems are built, they don’t get dismantled when administrations change. The surveillance infrastructure built for “counter-terrorism” in 2003 is now being used for immigration enforcement, predictive policing, employee monitoring, and civilian data management. What it’s used for next depends on whoever is in power.
How to reduce your exposure — step by step
You can’t fully opt out of systems like Palantir — your data exists in government databases whether you like it or not. But you can dramatically reduce the amount of new data you generate and how traceable it is. Here’s how:
Step 1: Switch to GrapheneOS
Your phone is the single biggest data source in your life. Stock Android reports your location, app usage, contacts, and browsing to Google constantly — data that ends up in systems accessible to intelligence agencies and law enforcement. GrapheneOS removes all Google telemetry, gives you per-app network controls, and prevents your phone from leaking data you don’t authorise.
Step 2: Use encrypted messaging — always
Regular phone calls and SMS are logged by your carrier and accessible through legal orders. Palantir’s systems can ingest call logs and message metadata. Switch to Signal or Molly for all private communication. For maximum metadata protection, use Session or SimpleX — they don’t require a phone number and route through decentralised networks.
Step 3: Use an always-on VPN
Your ISP logs every website you visit. This data can be subpoenaed or accessed through intelligence-sharing agreements. Use Mullvad or IVPN with kill switch enabled. On GrapheneOS, enable “Block connections without VPN” for zero-leak protection.
Step 4: Encrypt your DNS
DNS queries reveal every website you visit, even through a VPN if DNS leaks occur. Use DNS-over-HTTPS with Quad9 (9.9.9.9) or Mullvad DNS. Better yet, set it at the router level with a CryptHub privacy router to cover all devices on your network.
Step 5: Protect your entire network
Your phone might be encrypted, but your smart TV, security cameras, and IoT devices are wide open — and they all generate data that systems like Palantir can ingest. A privacy router encrypts all traffic from every device, applies VPN protection network-wide, and blocks telemetry at the gateway.
Step 6: Minimise your social media footprint
Palantir’s Gotham platform explicitly ingests social media data for intelligence analysis. Every post, every connection, every like is data that can be cross-referenced. Delete accounts you don’t use. Lock down privacy settings on the ones you keep. Consider whether you need them at all.
Step 7: Reduce your financial data trail
Bank transactions are accessible through legal orders and are exactly the type of data Palantir integrates. Use cash when possible. Use Monero for online purchases that accept it. Use prepaid cards for anything you don’t want tied to your name. Every traceable transaction is another data point in your profile.
Step 8: Limit what your phone broadcasts
Your IMEI and IMSI are transmitted to cell towers every few seconds. Palantir’s systems can access cell tower data through law enforcement databases. Disable 2G on your phone (Settings → Network → SIMs → Allow 2G → off on GrapheneOS/Pixel). Use airplane mode in sensitive locations. Carry a Faraday bag for moments when you need to be invisible.
Step 9: Use privacy-focused browsers and email
Chrome sends everything to Google. Gmail is fully accessible through FISA court orders. Switch to Vanadium or Brave with uBlock Origin. Use ProtonMail or Tuta for email. Use SimpleLogin for disposable addresses so your real email doesn’t end up in corporate databases.
Step 10: Understand that reducing data creation is better than trying to hide it
You can’t delete your tax records or your driver’s licence from government databases. But you can stop feeding new data into the system. Every Google search you don’t make, every social media post you don’t publish, every unencrypted call you don’t place — that’s data that never gets created, never gets stored, and never ends up in a system like Palantir. The best defence isn’t encryption. It’s minimisation.
iVPN — Subscription Voucher
Mullvad VPN – Subsciption Voucher
Frequently asked questions
Does Palantir have access to my personal data?
Palantir doesn’t collect data itself — it integrates data that governments and corporations already have. If you have a driver’s licence, tax records, a phone plan, or a bank account, your data exists in systems that Palantir’s software can connect. The danger isn’t that Palantir has your data — it’s that Palantir can cross-reference data from dozens of sources to build a complete profile of your life, relationships, habits, and movements.
Can GrapheneOS and a VPN protect me from systems like Palantir?
They protect you from generating new data that feeds into these systems. GrapheneOS stops your phone from reporting your location, app usage, and contacts to Google — data that’s accessible to intelligence agencies. A VPN prevents your ISP from logging your browsing, which can be subpoenaed. Encrypted messaging ensures your communications can’t be intercepted. These tools don’t delete existing data, but they dramatically reduce the flow of new information into the surveillance infrastructure.
Is Palantir operating in Europe too?
Yes, extensively. Palantir has a £330 million NHS contract in the UK, a £315 million deal with the UK Ministry of Defence, and has been secretly used by Dutch police since 2011. It operates NATO-compatible military systems and has partnerships with intelligence agencies across Five Eyes and 14 Eyes countries. European citizens are very much within reach of Palantir’s systems, both through direct government contracts and through intelligence-sharing agreements with the United States.
You can't unplug — but you can reduce the signal
Palantir isn’t going away. It’s more embedded in government infrastructure today than at any point in its history. The $10 billion Army contract, the ImmigrationOS platform, the NHS data system — these are decade-long commitments that will outlast any single administration or political cycle.
You can’t opt out of the databases your data already lives in. But you can stop feeding them. Switch to GrapheneOS. Encrypt your messages. Route your traffic through a VPN and encrypted DNS. Minimise your social media. Pay with cash or Monero. Carry a Faraday bag.
Systems like Palantir are most powerful when they have unlimited data. Every piece of information you keep out of the system weakens its profile of you. That’s not paranoia — that’s mathematics.
They’re connecting the dots on your life. Give them fewer dots to connect.








