The EU wants to decrypt all your data by 2030 — and how to protect yourself
Best secure phone 2025
Google Pixel 9 GrapheneOS VPN Encrypted
Google Pixel 9a GrapheneOS VPN Encrypted
Best secure router 2025
CryptHub V3 Portable 4G VPN Encrypted Router
CryptHub V2 Portable 4G VPN Encrypted Router
Let’s skip the jargon and talk about what’s actually going on.
The European Union wants to be able to read any encrypted message, file, or connection by 2030. Not just messages from criminals or terrorists. Any encrypted data they decide is “relevant.”
That means your WhatsApp chats, your cloud backups, your VPN, your phone’s stored data — all of it. If these plans go through, the technology that keeps your private life private will have a built-in weakness. By design.
Now, you might be thinking: “I’m not doing anything wrong, why should I care?” Here’s the simplest way to think about it:
Imagine the lock on your front door. Now imagine the government says every lock in Europe must come with a master key that police can use. Sounds reasonable — until you realise that criminals, hackers, and foreign spies will also find that master key. Because that’s what always happens.
That’s exactly what’s being proposed for your digital life. And unlike a house key, a digital backdoor can be copied infinitely and used from anywhere in the world.
How did we get here?
This didn’t come out of nowhere. It’s been building for years.
2022–2023: The EU proposed something called “Chat Control” — a rule that would force messaging apps to scan every private message you send. Yes, every message. The idea was to catch illegal content, but the only way to do this on encrypted apps like Signal or WhatsApp is to break the encryption itself.
Over 300 of the world’s top scientists and security researchers signed an open letter saying: this is technically impossible without making everyone less safe.
2024: After a huge backlash, the European Parliament blocked the proposal. Germany publicly opposed it. Most people assumed it was dead.
It wasn’t.
Then it came back — bigger
In June 2025, the European Commission published a new security strategy called ProtectEU. This time, the goal is much bigger than scanning messages.
The official documents are clear:
- Encryption is now described as a “challenge to law enforcement”
- “Lawful access” to encrypted data is framed as a strategic necessity
- The deadline is 2030 — not a “maybe,” a concrete target
And it doesn’t stop at messaging. The scope covers:
- End-to-end encrypted messaging (Signal, WhatsApp, Element)
- Encrypted cloud storage (Proton Drive, Tresorit, iCloud)
- VPN tunnels (Mullvad, NordVPN, any VPN)
- Device encryption (your phone, laptop, backups)
In plain English: they want the ability to read anything that’s currently protected by encryption. Everything.
This is not a conspiracy theory. These are published EU Commission documents with named strategies, institutional owners, and deadlines. You can read ProtectEU yourself on the European Commission’s website.

Wait, what is encryption? And how would they break it?
Before we get into the technical stuff, let’s make sure we’re on the same page about what encryption actually does. It’s simpler than it sounds.
Think of encryption like putting a letter inside a locked box. You have a key, the person you’re sending it to has a key. Nobody in between — not the postal service, not the government, not hackers — can open it. That’s end-to-end encryption.
Now, politicians talk about “lawful access” like it’s a simple switch. In reality, there are only three ways to give governments access to encrypted data, and all three make everyone vulnerable:
- Key escrow — Think: giving a copy of your house key to the government.
Every encryption key gets stored somewhere officials can access. Sounds fine until that storage gets hacked — then everyone’s keys are exposed at once. The US tried this in the 1990s with the Clipper Chip. Researchers cracked it. Scrapped. - Mandatory backdoors — Think: a hidden door in every house, by law.
Software must include a secret way in. But a hidden door doesn’t check who’s walking through it. If police can use it, so can hackers, criminals, and foreign spies. The NSA secretly added a backdoor to an encryption standard (Dual_EC_DRBG). When discovered, it undermined trust in an entire global system. - Client-side scanning — Think: someone reading your letter before you seal it.
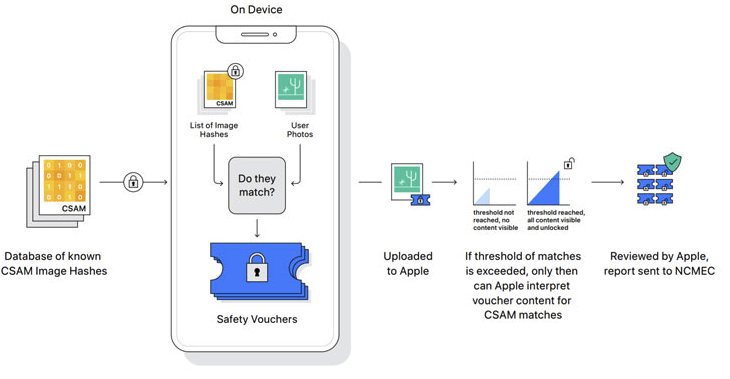
Your phone scans your messages and files before encrypting them. Apple tried building this in 2021 for iCloud Photos. Security researchers immediately showed it could be repurposed for political censorship and mass surveillance. Apple pulled it.
Here’s the bottom line: there is no backdoor that only “good guys” can use. This isn’t a political opinion. It’s a mathematical fact. Every serious cryptographer on the planet agrees on this.
What would actually be affected?
If these plans succeed by 2030, it’s not just one app or one service that’s affected. It’s everything that uses encryption — which is basically everything.
- Your VPN? Providers could be forced to weaken encryption or hand over your session data. This doesn’t just affect EU citizens — anyone using an EU-based VPN or connecting to EU infrastructure gets exposed too.
- Your messaging apps? Signal would have to add a way for governments to read your messages. That defeats the entire point. WhatsApp, Element, Telegram’s secret chats — all the same.
- Your cloud storage? Services like Proton Drive or Tresorit that advertise “zero-knowledge encryption” (meaning even they can’t read your files) would have to redesign their systems or leave the EU market.
- Your phone and laptop? Manufacturers could be pressured to build compliance tools that let authorities extract data before encryption kicks in. Basically, a government-mandated spyware hook in your operating system.
And once a weakness is built in, it applies to every user of that system. It doesn’t distinguish between a journalist’s phone and a criminal’s phone. Once the mechanism exists, it’s available to anyone who discovers it — including hackers, ransomware gangs, corporate spies, and foreign intelligence services.
History shows that mandatory vulnerabilities are always abused. Not hypothetically. Repeatedly.
“But it’s only for catching criminals, right?”
“It’s only for catching criminals” is always the argument. And it’s never how it stays.
Every single time a government has built mass surveillance infrastructure for a “narrow” purpose, the scope has expanded. Every time. Without exception:
- USA — Patriot Act, Section 215: Sold as counter-terrorism. Ended up collecting phone records on millions of ordinary Americans. We only found out because Edward Snowden leaked the documents.
- UK — Investigatory Powers Act (“Snoopers’ Charter”): Started as a serious crime tool. Now used by dozens of government agencies with weak judicial oversight.
- EU — Europol: Started with drug trafficking and terrorism in 1999. Its mandate has expanded steadily ever since, with broader powers and fewer checks.
The pattern is simple: first they build the tool, then they expand how it’s used. Once the infrastructure exists, there’s no going back.
This affects everyone: journalists protecting sources, lawyers with privileged communications, businesses with trade secrets, healthcare providers bound by GDPR, developers building secure systems, and every ordinary person who uses encrypted messaging, cloud storage, or a VPN.
Encryption protects everyone — or no one.
What can you actually do about it?
You can’t stop legislation on your own. But you can make your data as resilient as possible, regardless of what laws pass. Here are practical steps you can take right now:
✅ Switch to Signal or Molly for messaging. Signal is free, open-source, and the gold standard for encrypted messaging. On Android, try Molly — a hardened fork with extra protections. Turn on disappearing messages.
✅ Encrypt your cloud files before uploading. Use Cryptomator — a free tool that encrypts files on your device before they reach the cloud. Works with Google Drive, Dropbox, iCloud, or any provider. Even if someone accesses your account, they see gibberish.
✅ Get a VPN you can actually trust. We recommend Mullvad — no email required, accepts cash by mail, keeps zero logs, and has been raided by police who found nothing because there was nothing to find. IVPN is another solid choice. Always-on, kill switch enabled.
✅ Encrypt every device you own. Full-disk encryption on phone and laptop. Strong PIN or passphrase (minimum 8 characters, ideally alphanumeric). BitLocker on Windows, FileVault on Mac, LUKS on Linux.
✅ Consider GrapheneOS for your phone. It’s the most secure mobile OS available. Runs on Pixel phones. Hardened encryption, per-app network controls, sandboxed Google Play. It’s what we use ourselves and install for our clients.
✅ Switch to encrypted email. ProtonMail or Tutanota. Both end-to-end encrypted, both open-source. Gmail, Outlook, and Yahoo can read your emails. These can’t.
✅ Replace your ISP router. Buy your own, install OpenWRT, configure encrypted DNS (Quad9 or Mullvad DNS), set up a VPN at the router level. We sell pre-hardened routers ready to go.
✅ Use Tor for sensitive browsing. When you need real anonymity, Tor Browser bounces your connection through multiple encrypted relays. Don’t log into personal accounts through Tor — use it for things that need true privacy.
✅ Delete what you don’t need. Old accounts, old messages, old files in the cloud. The safest data is data that doesn’t exist. Less data on servers means less for anyone to access.
✅ Stay informed and push back. Follow the Electronic Frontier Foundation (EFF), European Digital Rights (EDRi), and the Chaos Computer Club (CCC). Sign petitions. Contact your MEPs. Donate if you can. Laws like this pass when people stay quiet.
The EU has set 2030 as the deadline. That’s five years away. The groundwork is being laid right now.
Start with one or two steps from the list above. You don’t need to do everything at once. But do something. Your privacy doesn’t protect itself.






